Synology VPN: Difference between revisions
Brian Wilson (talk | contribs) |
Brian Wilson (talk | contribs) |
||
| (One intermediate revision by the same user not shown) | |||
| Line 14: | Line 14: | ||
=== Config #1, remote lan at Wildsong office === | === Config #1, remote lan at Wildsong office === | ||
Config 1 uses Synology VPN to route traffic between the server and a '''Debian based router''' | Config 1 uses Synology VPN to route traffic between the server and a '''Debian based router''' to get packets to my | ||
home LAN. I need this set up to work through some generic router provided by Sonic. | home LAN. I need this set up to work through some generic router provided by Sonic. | ||
SYN <--> HQ | SYN <--> HQ Comcast router <--> ( INTERNET ) <--> eth1 [[Bellman]] eth0 <--> Wildsong LAN | ||
I can get ports opened on the HQ router but that can be difficult to do remotely. | I can get ports opened on the HQ router but that can be difficult to do remotely. | ||
=== Config #2, remote workstation === | === Config #2, remote workstation === | ||
| Line 37: | Line 33: | ||
Here is the [https://www.synology.com/en-us/knowledgebase/DSM/tutorial/Application/How_to_connect_to_Synology_s_VPN_Server_using_a_Windows_PC_or_Mac Synology tutorial]. Refer to the L2TP section. | Here is the [https://www.synology.com/en-us/knowledgebase/DSM/tutorial/Application/How_to_connect_to_Synology_s_VPN_Server_using_a_Windows_PC_or_Mac Synology tutorial]. Refer to the L2TP section. | ||
# | # enable L2TP for accounts in LDAP. | ||
# | # enable L2TP | ||
# | # leave most settings at defaults, but set range for dynamic addresses to 172.16.123.0 and authentication to PAP. | ||
# I set up a "pre-shared key". It's secret. | # I set up a "pre-shared key". It's secret. | ||
# Enable SHA2-256 | # Enable SHA2-256 | ||
Open UDP | Open UDP ports 1701, 500, 4500 on the firewall. | ||
NB, the firewall is not enabled on the NAS | |||
=== Mac === | === Mac === | ||
Latest revision as of 19:22, 13 June 2017
This content moved from Synology, to preserve it but I am not using the Synology VPN at this time.
The idea was to provide remote access to people using Windows and Mac OS/X.
We don't need to bridge networks together. Just one laptop at a time. See "config #2"
Overview
Configuring and testing the Synology VPN.
The Synology will be deployed in a remote office (HQ) and accessed from home offices (SAT). I need to set up a test network to try it out before deployment.
Config #1, remote lan at Wildsong office
Config 1 uses Synology VPN to route traffic between the server and a Debian based router to get packets to my home LAN. I need this set up to work through some generic router provided by Sonic.
SYN <--> HQ Comcast router <--> ( INTERNET ) <--> eth1 Bellman eth0 <--> Wildsong LAN
I can get ports opened on the HQ router but that can be difficult to do remotely.
Config #2, remote workstation
This will be the more typical set up. There is no satellite router for a LAN, just a single computer running the L2TP client.
SYN <--> HQ ROUTER <--> (INTERNET) <--> SAT ROUTER <--> HOME COMPUTER
I won't know what HQ ROUTER and SAT ROUTER are, but I can get ports opened on SAT ROUTER.
Basic server set up
Here is the Synology tutorial. Refer to the L2TP section.
- enable L2TP for accounts in LDAP.
- enable L2TP
- leave most settings at defaults, but set range for dynamic addresses to 172.16.123.0 and authentication to PAP.
- I set up a "pre-shared key". It's secret.
- Enable SHA2-256
Open UDP ports 1701, 500, 4500 on the firewall.
NB, the firewall is not enabled on the NAS
Mac
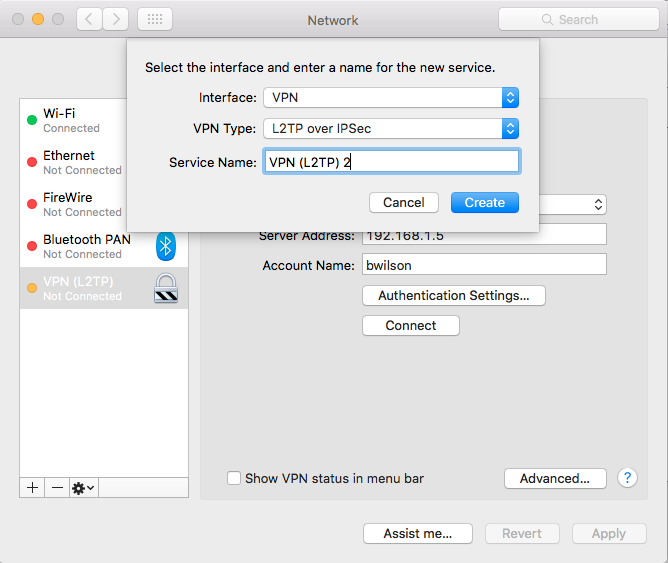
In Network preferences, create a new interface by clicking the "+" button and selecting VPN. Set it up like this; you could give it a better Service Name than I did, like "TrailPeople" for instance.
Server address should be your Internet address. I put 192.168.1.5 in for testing. Account name should be your user login name.
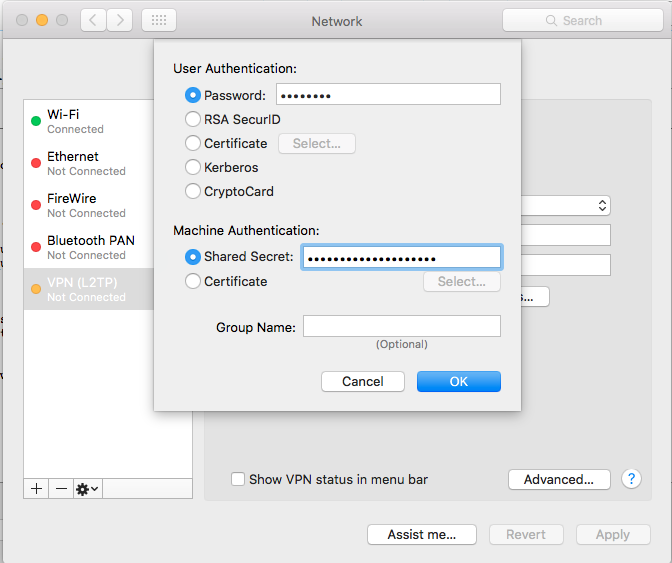
Click on Authentication Settings.
You need to use your regular Synology password and the secret.
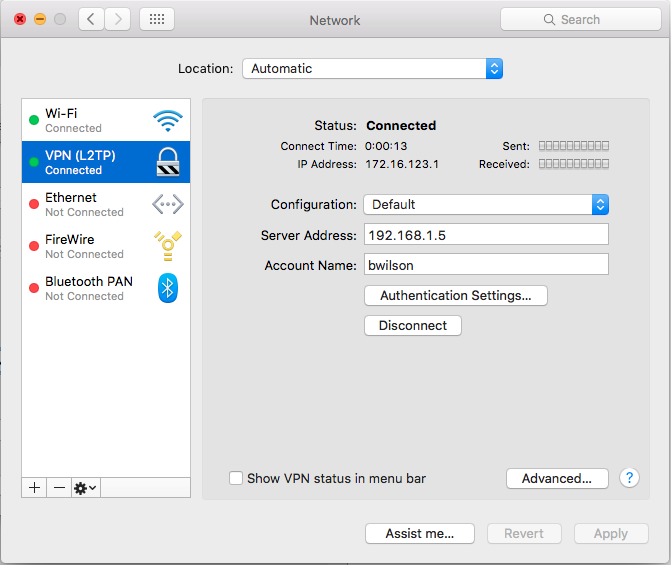
When you want to use the NAS from offsite you have to bring up the settings page and click "Connect". When you are done you should disconnect. This is what it looks like when you are connected.
DNS and DHCP
If I assign DHCP addresses out of this box, then I can also handle DNS requests (I push DNS server setting out) then I can also handle DNS for L2TP clients. That might work... routing has to be set correctly too though; we don't want ALL traffic for the remote client routed through the Synology. Just Synology traffic.
I could also just have the outside DNS always point at the inside addresses then any outside DNS would work -- you'd have to have a tunnel open but that's fine... this is far easier. We like "easier".
So for example.com
example.com and www.example.com are our hosted web site. It always resolves to the web host public IP diskstation.example.com is our NAS. It always resolves to 192.168.1.5
You can't reach the server from outside without the tunnel but that's by design anyway. So, that's what I will do.