OpenVPN: Difference between revisions
Brian Wilson (talk | contribs) mNo edit summary |
Brian Wilson (talk | contribs) |
||
| (One intermediate revision by the same user not shown) | |||
| Line 1: | Line 1: | ||
2022-03-24 '''Don't use L2 tunnels or OpenVPN anymore, use [[Wireguard]]. It's so easy set up it's not even worth looking at anything else. | 2024-12-14 I am setting up OpenVPN connection to Proton VPN as part of a class I am taking. | ||
The "drawback" is that you need to be running Linux or a Linux-based router like an EdgeRouter. | |||
2022-03-24 '''Don't use L2 tunnels or OpenVPN anymore, use [[Wireguard]]. It's so easy set up it's not even worth looking at anything else.''' | |||
The "drawback" is that you need to be running Linux or a Linux-based router like an EdgeRouter. | |||
These are some notes on how I manage OpenVPN. | These are some notes on how I manage OpenVPN. | ||
| Line 9: | Line 11: | ||
== Overview == | == Overview == | ||
'' | === ''Proton VPN'' === | ||
''I needed a VPN for testing in a class so I set up a virtual machine with a Kali Linux image, then downloaded the set up file for OpenVPN from <nowiki>https://ProtonVPN.com</nowiki> using my free account. Then as root I ran "openvpn setupfile.ovpn". It prompted me for special username/password credentials which are on my Proton account page, and there you go.'' | |||
''From the Kali guest operating system using "whatismyip.com", I can see I have a different IP address than at the Host level. As long as the ovpn session remains open, my traffic flows through the VPN server.'' | |||
''When I check the routing table on Kali, I see that it's put the default route through tun0 so all traffic goes out.Sure enough, even pinging the host computer no longer works.'' | |||
''2016-May This describes how I used to do it using OpenWRT.'' | |||
My Buffalo router is configured to keep a connection up to the work server at all times, and to route home traffic seamlessly across the connection to work, so that basically I always have access to all work resources from my home network. (And vice versa.) There are no firewalls or NAT limitation, when it's working I just see two networks routing packets to each other at OSI Layer 3. | I run OpenWrt on a Buffalo WZR-HP-G300NH router with OpenVPN on the router. At my co-lo I use a Mikrotik RB2011 there. My Buffalo router is configured to keep a connection up to the work server at all times, and to route home traffic seamlessly across the connection to work, so that basically I always have access to all work resources from my home network. (And vice versa.) There are no firewalls or NAT limitation, when it's working I just see two networks routing packets to each other at OSI Layer 3. | ||
It's possible to run the OpenVPN software as a client right on the computer, but the setup shines when it's on the routers. Traffic just goes across the link seamlessly for any computers located on either network. | It's possible to run the OpenVPN software as a client right on the computer, but the setup shines when it's on the routers. Traffic just goes across the link seamlessly for any computers located on either network. | ||
I have set up a separate page to talk about configuring [[OpenVPN between Mikrotik and OpenWRT]] | I have set up a separate page to talk about configuring [[OpenVPN between Mikrotik and OpenWRT]] | ||
Latest revision as of 03:18, 16 December 2024
2024-12-14 I am setting up OpenVPN connection to Proton VPN as part of a class I am taking.
2022-03-24 Don't use L2 tunnels or OpenVPN anymore, use Wireguard. It's so easy set up it's not even worth looking at anything else. The "drawback" is that you need to be running Linux or a Linux-based router like an EdgeRouter.
These are some notes on how I manage OpenVPN.
See also OpenL2TP, which I have not managed to get working yet. I got OpenWRT to talk to a MT router over PPTP but yick, still ended up with NAT and a firewall in there, so what's the point?
Overview
Proton VPN
I needed a VPN for testing in a class so I set up a virtual machine with a Kali Linux image, then downloaded the set up file for OpenVPN from https://ProtonVPN.com using my free account. Then as root I ran "openvpn setupfile.ovpn". It prompted me for special username/password credentials which are on my Proton account page, and there you go.
From the Kali guest operating system using "whatismyip.com", I can see I have a different IP address than at the Host level. As long as the ovpn session remains open, my traffic flows through the VPN server.
When I check the routing table on Kali, I see that it's put the default route through tun0 so all traffic goes out.Sure enough, even pinging the host computer no longer works.
2016-May This describes how I used to do it using OpenWRT.
I run OpenWrt on a Buffalo WZR-HP-G300NH router with OpenVPN on the router. At my co-lo I use a Mikrotik RB2011 there. My Buffalo router is configured to keep a connection up to the work server at all times, and to route home traffic seamlessly across the connection to work, so that basically I always have access to all work resources from my home network. (And vice versa.) There are no firewalls or NAT limitation, when it's working I just see two networks routing packets to each other at OSI Layer 3.
It's possible to run the OpenVPN software as a client right on the computer, but the setup shines when it's on the routers. Traffic just goes across the link seamlessly for any computers located on either network.
I have set up a separate page to talk about configuring OpenVPN between Mikrotik and OpenWRT
The basic concept of OpenVPN
You install an OpenVPN client and a set of keys on your computer. When you run the client, it creates a virtual network interface on your computer and connects it via an encrypted "tunnel" to our server at CDS Wireless.
When your computer needs to talk to a computer on the other site of the connection, the packets are sent through the tunnel. The OpenVPN software takes care of encrypting packets as they enter the tunnel and decrypting them on the other side as they leave the tunnel.
When the connection is in place, you get direct access to any resource that you'd be able to reach inside the office - including all file servers, desktop systems, telephones, and printers.
All data is encrypted when it is passing over the Internet. Anyone spying on the traffic out on the Internet sees only the encrypted data, but any program running on your computer sees just another normal network connection.
Set up notes for Windows clients
These are notes for users. If you are the network administrator skip ahead for information on creating the special files. This doc assumes that the sysadmin has generated a set of files for your personal use ahead of time, and put them on a shared file server in a known location.
You can download an OpenVPN client directly from the Internet at the Community OpenVPN page but will still need our special server key.
Installation
- Run the openvpn installer that you will find in the folder.
- Copy the files ourdomain.ovpn and ca.crt to C:\Program Files\OpenVPN\config\
- Get your own personal key files (client.key and client.crt) from the subfolder named after you. Put them in the config folder as well.
Usage
- Windows XP - Double-click the OpenVPN GUI to launch it. (This adds an OpenVPN icon to the tray, you won't see much happen.)
- Windows Vista or Seven - Right click the icon and tell it to run as Admin. (This adds an OpenVPN icon to the tray, you won't see much happen.)
- Right-click the OpenVPN icon in the tray and select "Connect". This should bring up the VPN tunnel.
- When you are done using AGI resources you should right-click / disconnect.
(Leaving it running all the time is a security hole.)
When the connection is running you should be able to access any system on the AGI network.
Macintosh: There is a compatible client called TunnelBlick available for Macintosh users. I have gotten it going but have not written it up here yet. It's very similar in that you have to drop the same config files into a folder on the Mac.
Set up notes for Linux clients
2017-04 Bellman notes: I added openvpn-up.sh and openvpn-down.sh scripts to /etc/network and I run them from the alseageo.conf script in /etc/openvpn
These scripts add and remove INPUT and FORWARD firewall rules and turn on/off MASQUERADE so that any host inside my network can use AGI resources when the tunnel is up.
Prerequisites
Install the required software.
sudo apt-get install openvpn sudo apt-get install network-manager-openvpn sudo apt-get install unzip
Request keys from me. I will generate them and send them to you. When the file arrive unzip it someplace convenient for you.
unzip hupi_openvpn.zip
Now you're ready to configure opnvpn.
Network connections
In the "Network Connections" control panel, select the VPN tab.
Create a new VPN connection (click Add button) and use the OpenVPN option.
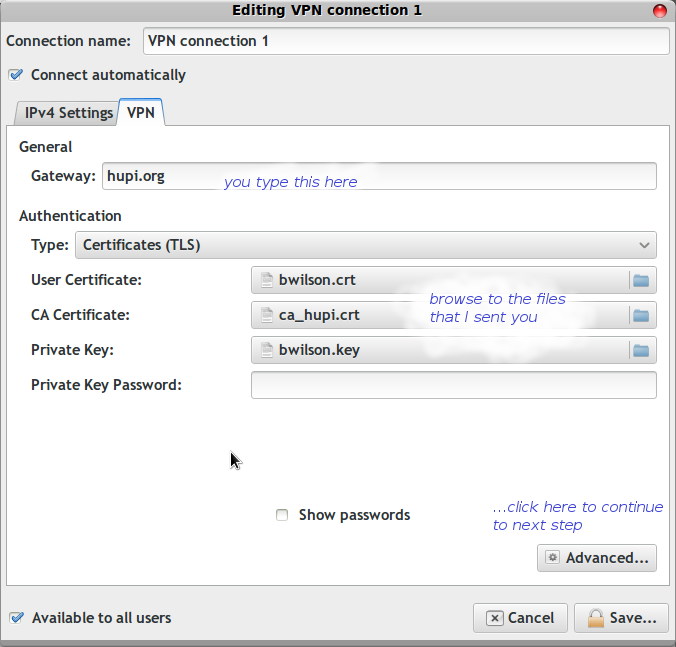
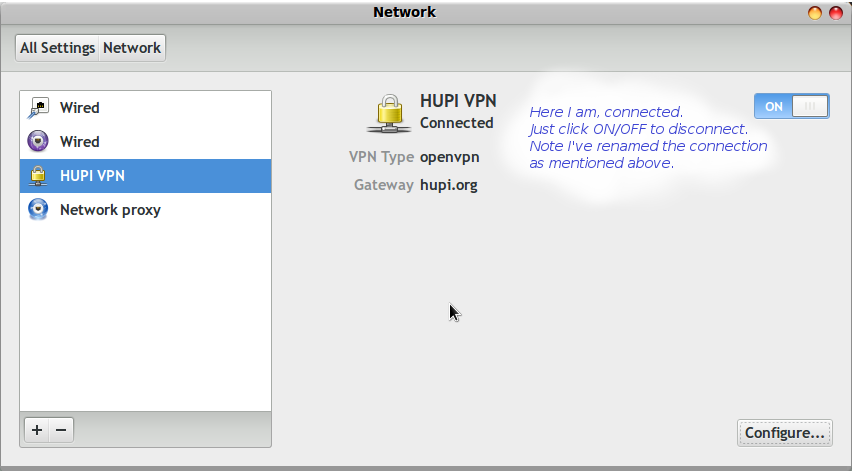
Default name is "VPN connection 1", you can rename if you want.
Point it at the key and certificate files from the zip. Like this:
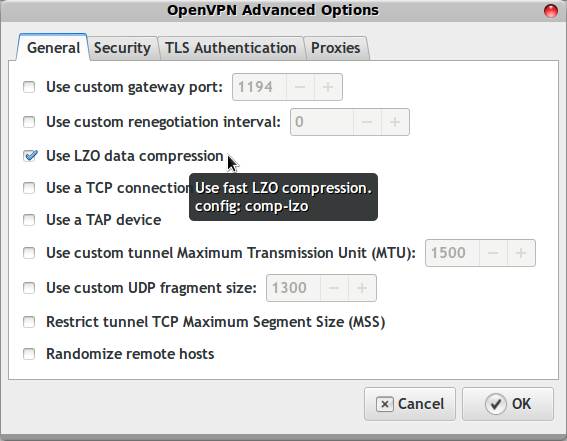
Advanced settings
After you click the Advanced button, on the General tab turn on LZO compression
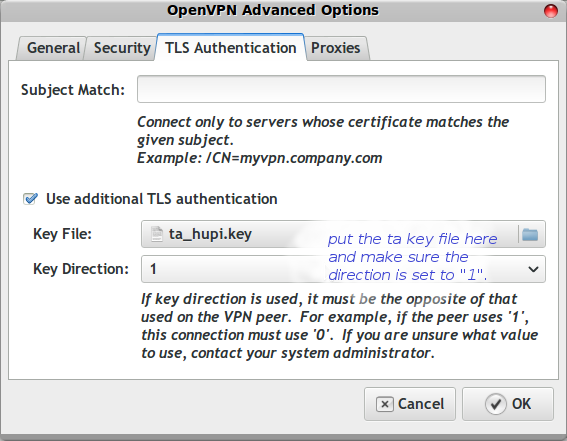
Then click on the TLS Authentication tab and point the TLS entry at the file I sent
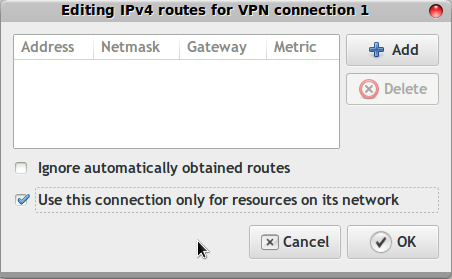
Routing
Now switch to the IPv4 Settings tab.
Down in the right corner, click on the "Routes..." button.
Check Use this connection only for resources on its network.
If you leave this unchecked you will ONLY be able to hit the hupi.org server when the VPN connection is on.
Not a disaster but inconvenient.
Starting and stopping the VPN connection
There is a Connect automatically option but it's better security to control the connection manually. Only bring up the connection when you need it.
Adding the above settings will cause a new section to appear in your network manager. On my Linux Mint computer I can see it in the tool panel at the lower right... it's off somewhere else on other desktops.
You can also bring up your Network settings to start or stop a VPN connection.
Either way when the connection comes up, your system will tell you via a pop up notification
that says VPN connection has been successfully established.
Then you can test it by going to this link. http://172.16.0.1/
Using the connection
You can use the connection for network services that I don't expose to the wider Internet.
SSH: ssh will work over VPN from any place. Normally it's locked down to a few source addresses for security.
FTP: You can use any old FTP client over VPN. Only SFTP is allowed over the Internet connection.
POP3 and IMAP: You can read email boxes. Not that we actually use this at the moment.
I might allow direct MySQL and PostgreSQL connections if it becomes useful.
Details for sysadmins
These are notes for your system administrator.
Server set up
https://wiki.debian.org/OpenVPN
See also regarding systemd: https://unix.stackexchange.com/questions/148990/using-openvpn-with-systemd#149003
cd /etc/systemd mkdir [email protected] cd openvpn\@.service.d/ emacs local-after-ifup.conf cd /etc/tmpfiles.d/ emacs local-openvpn.conf systemctl disable [email protected] systemctl enable [email protected] cd /etc/systemd/system/multi-user.target.wants/ ls open*
Debugging a connection
On a Windows client in a command window, do ipconfig /all. This is the output from a desktop machine.
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\Documents and Settings\bwilson>ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : Umatilla
Primary Dns Suffix . . . . . . . : ourdomain.com
Node Type . . . . . . . . . . . . : Broadcast
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : ourdomain.com
crestviewcable.com
Ethernet adapter Wireless Network Connection:
Media State . . . . . . . . . . . : Media disconnected
Description . . . . . . . . . . . : Intel(R) PRO/Wireless 3945ABG Network Connection
Physical Address. . . . . . . . . : 00-1C-BF-A3-84-40
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . : crestviewcable.com
Description . . . . . . . . . . . : Intel(R) 82566MM Gigabit Network Connection
Physical Address. . . . . . . . . : 00-1C-25-72-5F-65
Dhcp Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IP Address. . . . . . . . . . . . : 192.168.0.2
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.0.1
DHCP Server . . . . . . . . . . . : 192.168.0.1
DNS Servers . . . . . . . . . . . : 64.77.202.9
69.60.160.196
68.87.69.146
Lease Obtained. . . . . . . . . . : Tuesday, May 25, 2010 8:16:07 AM
Lease Expires . . . . . . . . . . : Friday, May 28, 2010 8:16:07 AM
Ethernet adapter Local Area Connection 2:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : TAP-Win32 Adapter V9
Physical Address. . . . . . . . . : 00-FF-66-21-BC-21
Dhcp Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled .
Creating a key bundle for a new client system.
This is what I do to create the key pair that I give you.
1. Log into the OpenVPN server and 'su' to get root access.
2. Do this:
cd /etc/openvpn/easy-rsa source vars
3. Run the command "./build-key client" where client is the client's name, like bwilson or jsmith. You can accept most of the defaults in this command.
4. Use the client's name (eg bwilson) when it asks for "Common Name". Say yes when it asks if you want the key signed. Say yes when it asks for commitment.
5. Bundle the files for the remote user.
make_bundle bwilson
6. Email the encrypted file to the user as an attachment.
mpack -s "Your keys to HuPI.org" -d instructions.txt hupi_openvpn.zip [email protected]
The script to make a bundle looks like this:
#!/bin/bash VPNUSR=$1 if [ -z "$VPNUSR" ]; then echo "usage: make_bundle username" exit -1 fi echo Building bundle for $VPNUSR if [ ! -f "keys/$VPNUSR.key" ]; then echo "No key exists for $VPNUSR, did you make keys yet?" exit -1 fi SSHKEY=/home/$VPNUSR/.ssh/id_rsa.pub if [ ! -e "$SSHKEY" ]; then echo "$VPNUSR does not have an SSH public key in $SSHKEY." exit -1 fi if [ ! -d hupi_openvpn/keys ]; then mkdir -p hupi_openvpn/keys fi cp hupi-client.conf hupi_openvpn echo cert keys/$VPNUSR.crt >> hupi_openvpn/hupi-client.conf echo cert keys/$VPNUSR.key >> hupi_openvpn/hupi-client.conf cp ../ta_hupi.key hupi_openvpn/ cp ../ca_hupi.crt hupi_openvpn/ cp keys/$VPNUSR.crt hupi_openvpn/keys/ cp keys/$VPNUSR.key hupi_openvpn/keys/ rm -f hupi_openvpn.zip cd hupi_openvpn zip -r ../hupi_openvpn.zip * cd .. rm -rf hupi_openvpn/* ls -l hupi_openvpn.zip
The client template file looks like this
client dev tun proto udp tls-auth 1 remote hupi.org 1194 name of the server you are connecting too resolv-retry infinite nobind user nobody group nogroup persist-key persist-tun ca keys/ca_hupi.crt comp-lzo verb 3 mute 20
Network config details
The main OpenVPN server is at 10.8.0.1
By default OpenVPN will create a point to point link for each client from a pool in the same subnet, for example 10.8.0.13 and 10.8.0.14. From the client you can always see the OpenVPN server at 10.8.0.1 It's possible to nail down the client to a particular subnet if you want two way connections so that you can get access to your home machine from the office.
Server set up
Currently the main file server (running Linux and Samba) is running as a OpenVPN server, so that outside workers can get a VPN connection into our LAN. In the meantime there are NAT rules to make routing work on Kilchis.
On the file server you need to adjust these files
/etc/openvpn/server.conf /etc/dnsmasq.conf /etc/network/interfaces /etc/network/firewall.sh
/etc/openvpn/server.conf
At work, I run network numbers in the range 10.1.10.x. At home I use 192.168.123.x. The OpenVPN connections are 10.x.x.x, usually 10.8.0.x but for my own connection I use 10.128.x.x
Here are the parts I changed / added. I run everything over UDP so I have "proto udp" uncommented. I use the 'tun' device so I have the "dev tun" line uncommented.
# Certificates and key ca ca.crt cert ourdomain.crt key ourdomain.key # This file should be kept secret
# At work - internal LAN push "route 10.1.10.0 255.255.255.0"
# Brian Wilson at home (see also ccd/bwilson) route 10.128.0.0 255.255.255.0
# Certain Windows-specific network settings # can be pushed to clients, such as DNS # or WINS server addresses. CAVEAT: # http://openvpn.net/faq.html#dhcpcaveats push "dhcp-option DNS 10.8.0.1" push "dhcp-option DOMAIN ourdomain.com"
OpenWrt firewall fix
The problem: I want a tunnel to a client site to access machines there but want normal traffic to go over the Internet.
The firewall on OpenWrt is zone based, it's a little weird.
I was able to create a new zone (alseageo) and put the VPN tunnel into it and then set it to forward traffic from "alseageo" to "lan". But when I tried to set up traffic to go the other way "lan" to "alseageo", it removed the connection from "lan" to "wan". No more Internet!
I found a work-around to get it going was to ignore the confusing zone set up and add a separate iptables rule. In LUCI, Network -> Firewall -> Custom Rules, it looks like this:
# Send AlseaGeo traffic over the tunnel iptables -I zone_lan_forward 1 -j ACCEPT -s 192.168.1.0/24 -d 10.1.10.0/24
The file on the router containing these rules is /etc/firewall.user
This says any traffic coming from my LAN (192.168.1.x) that is headed for the remote network (10.1.10.x) is accepted. I was able to figure out the name of the zone by listing all the rules from a shell with "iptables -L -n".
Troubleshooting
Check the contents of the /etc/openvpn/openvpn.log and openvpn-status.log files.